Lightning Network
Anonymity and Onion Routing
Despite the initial intentions, when a technology is developed it may be used for good or bad. If a criminal conceives of a way to exploit it, they will. There are those that believe cryptocurrencies should be banned due to their appeal to criminals. Despite them not being as anonymous as many believe, it is still a stigma that prevails. However, the idea that bans should occur is flawed. Many technologies used in our everyday lives can be used in inappropriate manners. We simply must adapt and develop the necessary securities to protect one another from those that wish to do harm.
TOR within the Lightning Network
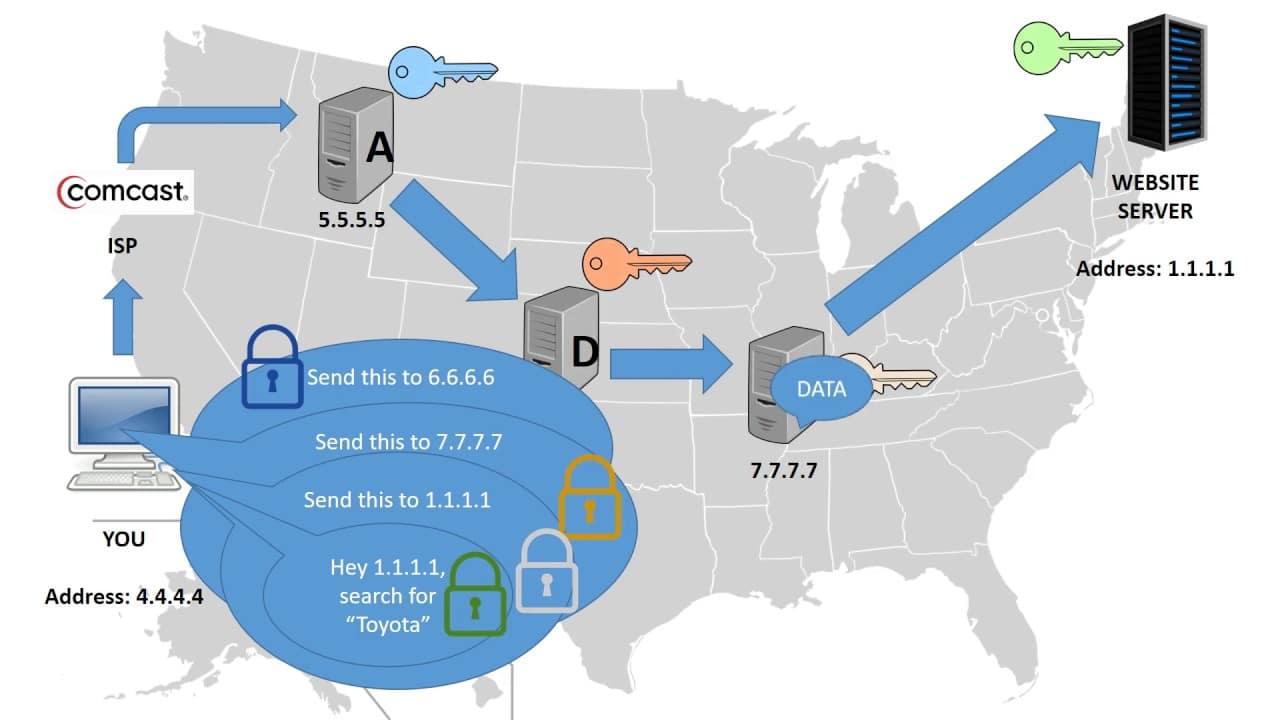
When speaking of the Lightning Network, this rings especially true. A main part of what makes the Lightning Network tick is the use of Onion Routing. This is a technology that brings a high level of anonymity to users of the network.
Simply put, it works by encapsulating data into a layered package. This means encrypting data being sent to another, and putting multiple layers of encryption on it. The data will be sent to destination via multiple relays or ‘hops’. The data will hop to a relay, which will ‘peel’ off a layer of encryption, revealing the next hop along its path. It will then be forwarded to the next hop. Each hop is unable to view the data, only the location of the hop immediately prior, and after itself. Eventually the data will reach the destination when there are no more layers to be peeled. As each hop can only see on either side of itself, there is no way to know who the original sender, or receiver is. In doing this these communications are now anonymous.
Origins
The origins of Onion Routing date back almost 3 decades. The technology in its earliest form was actually developed by the United States Naval Research Laboratory (USNRL). Throughout the development of the protocol over the years, government funding is what has facilitated the process. It is only in recent years with the public adopting the technology that government regulators have sullied its use.
Anonymity a growing concern
The use of this protocol in the Lightning Network is important for many reasons. One of them simply being that the public at large needs to become aware of the need for privacy. In a world overrun by social media, and targeted advertisement, most are blissfully unaware that they are being spied on. Consumer data is often collected and sold to the highest bidder. Unfortunately not even the people we trust with our data can be trusted. Central bodies controlling our data pools are often the subject of hacks. When this happens, everyday people’s sensitive data is exposed for the world to see. Below are a few of the hacks that have been seen in recent years.
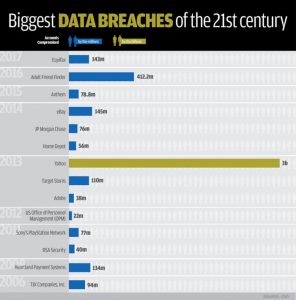
A few of the largest lapses in security in recent years.
It is obvious that even the most well-known companies cannot be trusted with securing our data.
There is also the ideological belief that data pertaining to ourselves belongs to us. No other should be able to profit off of its collection and/or sale. That right should remain at our discretion. As a result of the revelations that they sold off consumer data, Facebook recently saw their shares plummet. After releasing Q2 figures far below what investors hoped for, the company experienced a sell off unprecedented in the world of finance.
It is for reasons such as these that the argument for anonymity can be made. With our world becoming increasingly interconnected through ‘smart-devices’, these types of hacks will only continue. As this occurs, solutions such as the Onion Protocol will become even more important.
Potential for misuse
As stated, any new and useful technology can be used for ill-will. Despite the beneficial and necessary anonymity that Onion Routing can bring, this anonymity can obviously be used for doing bad things. Things of this nature may include,
– Drug transactions
– Weapon sales
– Sex trade dealings
– Counterfeight sales
The list goes on and on. In the world of crypto, the Onion protocol is most commonly known due to the infamous Silk Road. Operating as an online bazaar for illegal goods and activity, this dark-web site utilized primarily Bitcoin to fund its operations. Its users would rely on Onion Routing to maintain their anonymity while utilizing the site. It is due to this site that anonymity within crypto is often brought up as a concern for regulators.
In a recent interview with Bloomberg, it was stated by the DEA that crime now accounts for less than 10% of Bitcoin transactions. A far cry from the estimated 90% during Silk Road’s heyday. 10% is still 10% too much however, and must be taken into consideration when implementing protocols such as Onion on the BTC network.
If we banned every technology that could be used for bad things, we would still be living in the dark ages. Regulators need to embrace the potential benefits that technologies like the Onion Network and the Lightning Network provide. It is a fine line between regulation and dictatorship. Technologies such as this are what will give us back some semblance of the privacy we are entitled to; The privacy that has been eroding since the advent of the internet.